We use cookies to help our site run smoothly. Feel free to review our Privacy Policy for further details.
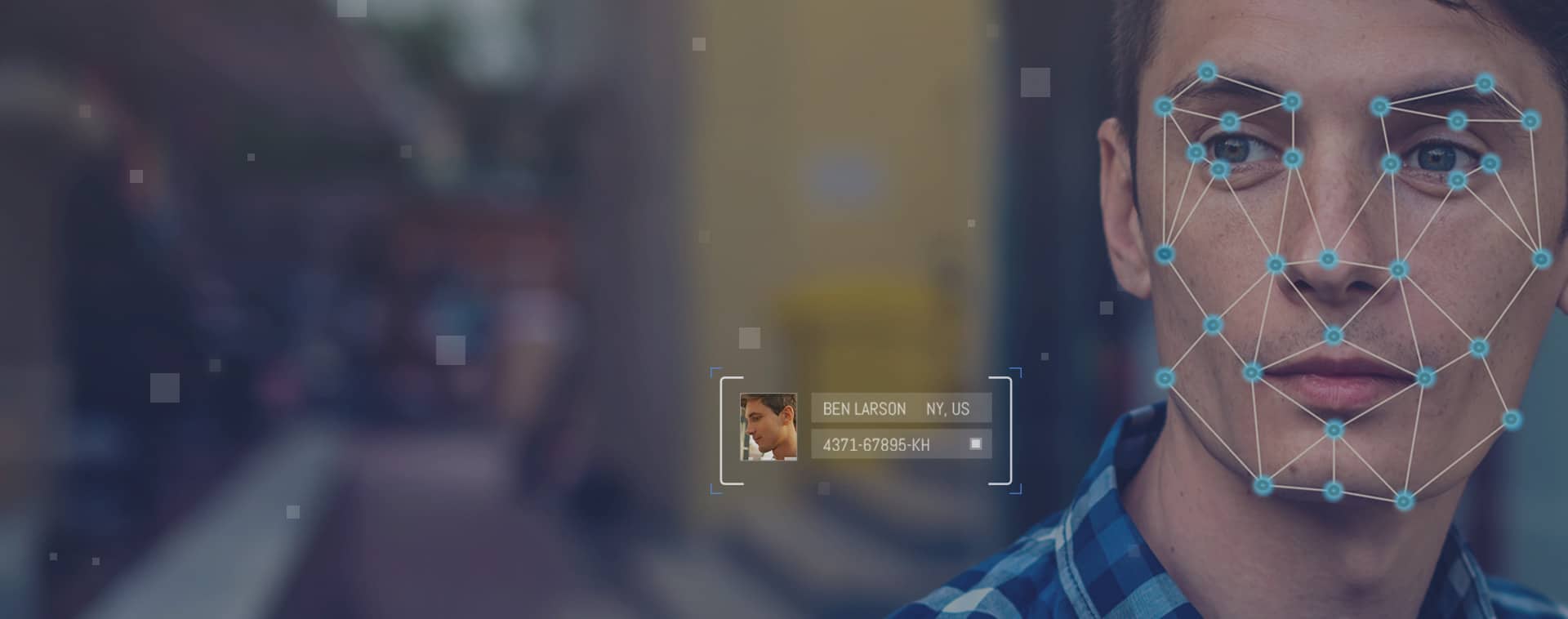

Traditional methods of photo protection – encryption, pixelization, blurring and others – limit a photo’s usability and can even ruin its appearance. And with today’s super resolution and parrot recognition techniques, these methods can’t fully protect against facial recognition.
D-ID enhances privacy and ensures regulatory compliance by removing unnecessary sensitive biometric data and personally identifiable information from facial images. Completely seamless and transparent, a D-ID protected photo looks no different to the human eye. Yet D-ID photo protection cannot be decrypted or reverse-engineered – outsmarting even the most advanced facial recognition engines.

De-identified photos by D-ID offer protection against facial recognition software. This means that even in the event of a data breach, facial recognition software cannot match a D-ID-protected photo to any identity. This lowers the risk associated with breaches, as well as the overhead of protection and remediation.
The D-ID de-identification system protects biometric databases while still enabling one-to-one authentication – all leveraging the same core technology. Compatible with any facial recognition engine, D-ID++ allows for reliable face authentication without compromising privacy or using actual sensitive biometric data.

D-ID++ keeps stolen or leaked facial images protected at all times – lowering risk to privacy since identities cannot be matched to a protected photo

Offered as an upgrade, D-ID++ is ideal for finance, government, access control, devices and more

Implementing D-ID++ enhances compliance with GDPR and other privacy regulations since no Personally Identifiable Information (PII) is stored on the facail images
Rather than enrolling an original identifiable photo, D-ID creates and stores an image or representation together with unique encrypted instructions. When authentication is required, facial matching is performed between the stored protected image/representation and the newly-captured image. Authentication is confirmed when both de-identified templates match.
D-ID de-identification instructions serve as a one-way hash function with no backdoor. Thus, reverting to the original image is impossible. Even if a device is stolen or an unauthorized user accesses the biometric database containing these instructions, de-identified photos remain fully protected by the one-way function.